컨슈머
- VGA FAN Gaming Lighting
- Capacitive Water Level Detection
- MA35H0 HMI Ordering Machine
-
NuMaker-Lighting-ARGB 개발 키트

-
Magic Board

-
NuEzAI-M55M1 개발 플랫폼

-
스마트 ITO 패널 솔루션

- Smart HMI
- USB4® 장치용 리타이머 IC
- HMI 플랫폼 및 그래픽 라이브러리 소개
- 게임 조명 및 냉각 팬 제어
- 새로운 HMI 플랫폼 NuMaker-HMI-MA35D1
- 반려동물용 GPS 추적기
- 두유 제조 드라이버
- CSP MOSFET
- TWS 충전
- M031BT 듀얼 모드 게이밍 마우스 솔루션
- 4 in 1 스마트 잠금 장치
- 헤드셋
- 유아 용품
- DSC / DVC
- DVR
- ELA
- 게임 콘솔
- 가전 제품
- 미디어 박스
- 초소형 프린터
- 보안 패널
- 스마트폰 결제
- Smoke / CO 감지기
- 사운드 바
- 토이
- 베이비 모니터 비디오
- 음성 인식
- 난방 주방 용품
- 무선 충전
- 하프 브리지 인덕션
- 스마트 프로젝터
- 레이저 TV
- 6 클로 로봇
- 스마트 플러그
- USB 자동차 운전 시뮬레이션 시스템
- 에어 마우스
- 디지털 전화기
- 태블릿
- 스마트폰
- 워키토키
산업용
- Low Power and Auto-Operation Mode Platform
- MA35D1 Dual-OS (RTOS & Linux) Application Demonstration
-
N9H31 HMI 플랫폼

-
MA35D0 산업용 게이트웨이 플랫폼

-
MA35H0 산업용 HMI 플랫폼

- ARGB Fan Driver
- Industrial Weight scale
- MA35D1 HDMI 동영상 재생
- NUC980 OpenWrt 그래픽 게이트웨이
-
DALI Ecosystem - 제어 장비 및 장치

-
DALI Ecosystem - 애플리케이션 컨트롤러

-
공기청정기

- 엣지 디바이스용 대역 외(OOB) 관리 솔루션
- 차량 번호판 인식용 엣지 컴퓨팅
- USB Type-C PD 3.0 TCPC 및 TCPM 솔루션
-
5G 기지국용 RF-GaN PA 모듈

- Servo 드라이버 모듈
- 엘리베이터 콜 보드
-
터치 키 온도조절기

- LoRaWAN ECO 시스템
- 대화형 휴먼 머신 인터페이스 솔루션
- 플러그 앤 플레이 산업용 계측 개발 플랫폼
- IoT 개발 플랫폼
- NB-IoT IoT 개발 플랫폼
- 산업용 원격 터미널 장치
- 스마트 수도 계량기
- 라벨 프린터
- 얼굴 인식 출석 기기
- 2D 바코드 스캐너
- 카드 리더기
- eBalance
- eBike
- 전기 계량기
- 얼굴 인식기
- 지문 인식기
- 선풍기 / 실링팬
- 가스 계량기
- 열 측정기
- POS
- QR 코드 스캐너
- 수도 계량기
- 8x8x8 LED 큐브
- 출입 통제 시스템
- 엘리베이터 제어 시스템
- LED 디스플레이
오디오/비디오
- NSR Smart Audio Control and GPIO Expansion Solution
-
NSC74 기능 시연

-
NSP2340A03G 기능 시연

- 멀티 채널 오디오 DSP
- NAU83G60 스마트 앰프
- NSC Series Voice Assistance Solutions
- 터치 솔루션을 탑재한 NSP2340T 음성 지원
- 스마트 오피스 UC 헤드셋 솔루션
- 스마트 오피스 UC 스피커폰 솔루션
- NSP 시리즈 음성 지원 솔루션
- 소음 감소 및 에코 캔슬레이션 솔루션
- 데모 보드 템플릿 - ISD2361
- 블루투스 오디오
- iPhone / Android 도킹
- TV Audio
- 와이파이 A / V 스트리밍
- 무선 마이크
- 무선 스피커
CCTV VPN 보안 모듈
Recently, Cyberattacks on CCTV and IP Camera systems have been getting more and more important since the potential attacks to the surveillance systems are highly interested in hackers’ society. For example, an U.S. ally observed a malicious actor attacking the U.S. State Department computer systems. In response the NSA traced the attacker’s source and infiltrated their computer systems gaining access to their CCTV cameras from where they were able to observe the hackers’ comings and goings. Novoton has noted this problem well for a period so we together with our partner, Security Platform Incorporation – Korea,to provide a secure CCTV VPN solution for the industry.
- What’s the Pain - Trade-off Among Cost, Security and Implementation
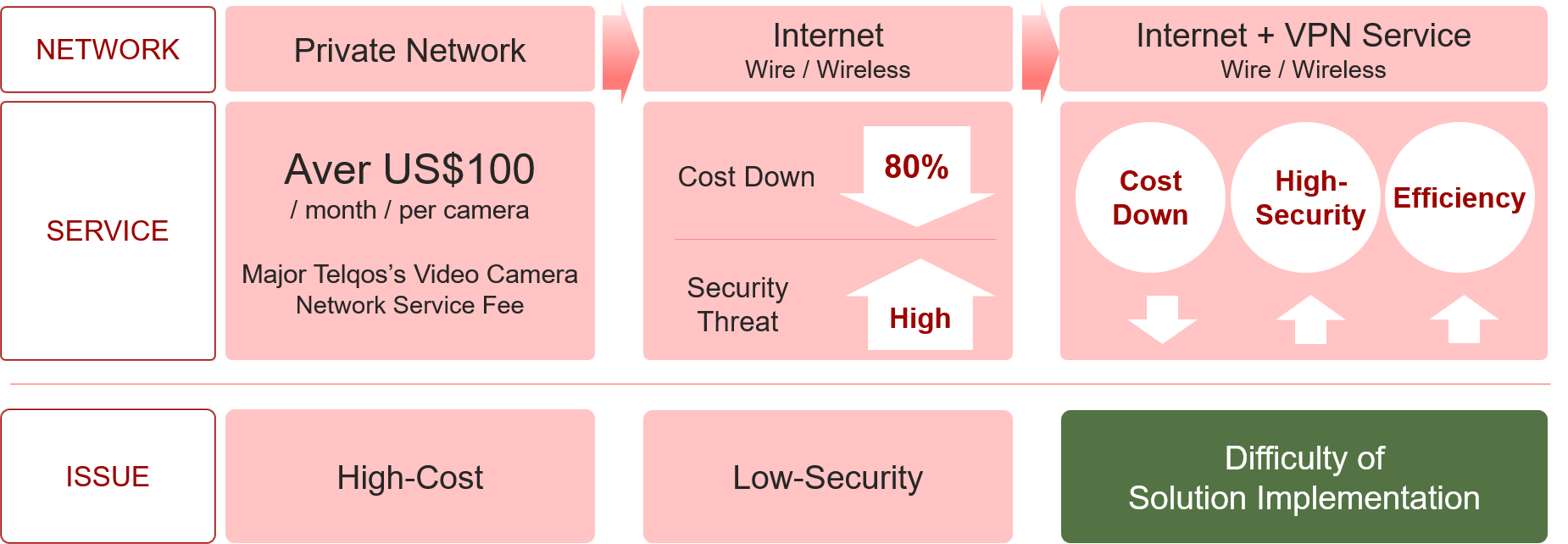
- Features
| Addressed Market Challenges & Opportunities | |||
| Enhanced Security | Remote Access Control | Cost Effective | Endpoint DLP |
|
|
|
|
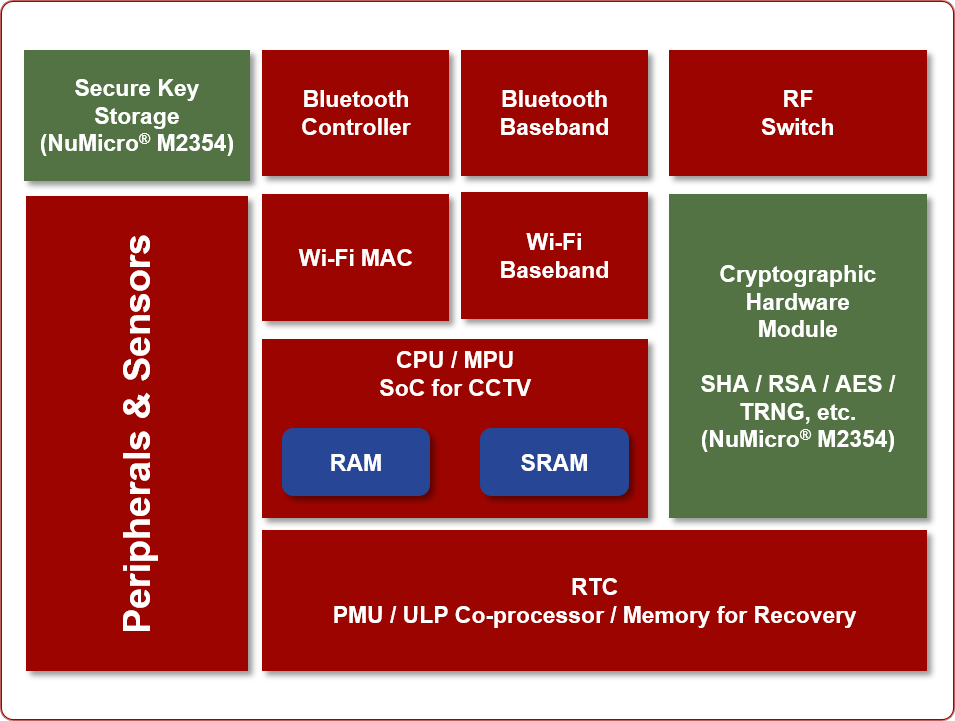
- System Block Diagram
M2354 IoT Platform with Trusted Firmware-M
 |
|
 粤公网安备 44030502010001号
粤公网安备 44030502010001号